How to Identify and Handle Spam
None of us like spam and we work hard to protect you from spam as much as possible. We have multiple filters in place that block roughly 40 – 60% of all e-mail as spam. In designing the filters, we seek to strike a very delicate balance between stopping as much illegitimate e-mail as possible while also ensuring we allow legitimate e-mail. While we are continuously working to improve the anti-spam systems, we will never be able to block all spam coming to you. Additionally, spammers are constantly changing their techniques to bypass our spam filters and we are constantly adjusting the filters to thwart their changing approaches.
Knowing that we can never stop all spam, this article is intended to help you better identify and know what to do with spam.
Once a spam email is identified, there is no need to notify us. You can simply delete the email. (By the time we would block a spammer, they have usually moved on to another e-mail address, rendering our block ineffective.) If you are unsure if an email is spam or not, please submit a ticket for us to evaluate it for you.
There are four main things to look for when identifying spam. The examples below are real spam e-mails, but they are modified to remove identifying information. Let us take a look at some of the most common examples of spam:
1. Address Spoofing
The spammer is misrepresenting the e-mail address they are using or the links they are telling you to click. The spammer wants you to believe that the e-mail came from a particular e-mail address, when it actually came from a different address.
Example 1 – The spammer is trying to make you think that the e-mail is coming from your company when the e-mail address reveals it is coming from somewhere else.
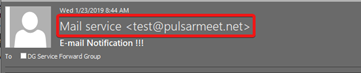
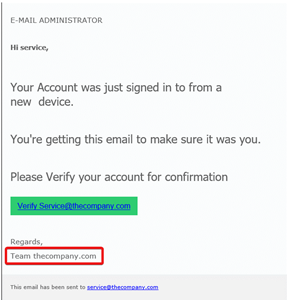
In the example below, the email signature says it comes from Team thecompany.com. However, in the From field, the actual sender email is entirely different: test@pulsarmeet.net.
Example 2 – The spammer is trying to get you to click on a link that takes you somewhere other than where they say it will.
In the example below, you can see that the link says that you are verifying an e-mail address but, when you place your mouse over the link, you can see that it will not take you to an address that is related to your company. (NOTE: DO NOT CLICK ON THE LINK.)
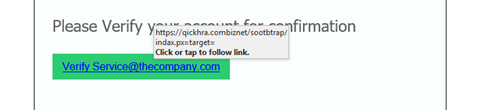
In the example above, we see that the link would take us to qickhra.combiznet, not the company.com.
2. Fear
The spammer is playing on your fear or is trying to intimidate/threaten you into an action.
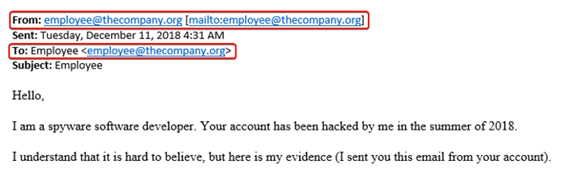
Example 1 – The spammer is trying to make you think your email account has been compromised.
In the example below, the spammer is spoofing the email address to make it look like it came from you. They also try to prey on your fear of exposing private information to get you to take some sort of action.
Example 2 – The spammer is trying to scare you with information only you supposedly know.
This is an extension of the previous example where the spammer is sharing information with you (ie. a password) that only you should know. When a service that you use (ie. FaceBook, LinkedIn, etc.) is hacked, the hackers are, often, able to get a list of credentials that were used on the hacked service. Spammers purchase lists of these credentials on the dark web then use the credentials to try and hack into your accounts (if you are using the same password elsewhere) or to send you an e-mail, telling you that they know your password.
As such, these emails may contain legitimate credential information, such as old usernames and passwords, in an attempt to trick you into thinking the email threat is legitimate. They will usually also request money.
Although the threat can be ignored, if the password listed matches one you currently use, we suggest that you immediately change that password everywhere it’s currently used. This is also an example of why is it optimal to never reuse passwords…every service you should use a unique password so a hack of one system does not give the hacker a password you use elsewhere.
3. Spelling and Grammar
Much of the spam comes from non-native English-speaking countries. As such, spelling and grammar can often tip you off to spam.
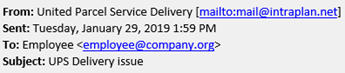
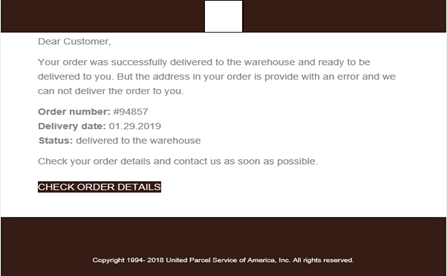
Below is an example that supposedly comes from UPS.
There are three issues that stand out:
- One of the first issues you can see is that the punctuation and grammar are a little off. In this case, you can see it in the line that says: “your order is provide with an error.”
- The email was supposedly from UPS but, as we learned in the spoofing section, we can see that the actual sender is mail@intraplan.net.
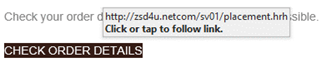
- In the screenshot below, when you place your mouse over the CHECK ORDER DETAILS link, it shows the website to be zsd4u.netcom which is not ups.com.
4. Escalation
Spammers will often start off very vague, simulating an e-mail sent from a phone and, often, from a person of importance. Their goal is to get you to engage them so they can get you do something, such as buy giftcards, disclose sensitive information, etc.
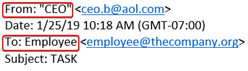
In the e-mail below, the spammer is intentionally vague, pretends to be from a cell phone and pretends to be the CEO. Their goal is to get you to just reply to the e-mail where they will ask you to do something.
Note that replying will also confirm to the spammer that your email address is legitimate and that you are vulnerable to such attacks. This will result in you receiving even more spam.

Below is another example. In this one, they are much more vague and brief.

Here are some tips to identify that this is spam:
- In both examples above, you will notice that the sender is from a different domain @aol.com instead of the actual company @thecompany.org.
- Spammers will often have the correct names of staff members to impersonate, but the sender address is typically spoofed and doesn’t match the actual person’s email address.
Business e-mail should, in most every case, come from your e-mail domain, not from other places, such as aol.com, gmail.com, etc. If you are ever in doubt of the legitimacy of this kind of e-mail, contact the person directly. You can call them, send them a new e-mail or forward the suspicious spam to the e-mail address that you know to be legitimate for that person. (ie. If the CEO is John Doe and your domain is mycompany.org, send an e-mail to jdoe@mycompany.org and ask if the e-mail is legitimate.)
Conclusion
We hope this article was helpful and raised your awareness of techniques spammers use to try to take advantage of you.
As mentioned at the beginning, if you identify an email as spam, please ignore and delete the email. It usually doesn’t do much, if any, good for us to block a spammer…by the time we block them, they have moved on to another e-mail address.
If you are ever unsure about whether a particular email is spam or not, please send us a ticket with a copy of the suspicious e-mail. Our support team will be happy to help you determine if it is spam or not.
